What is Internet Authentication?
Recently, the Internet has been covering more and morespheres of our life. Almost everything can be done using this resource. For example, pay for utilities, transfer money to another city, replenish the account on a mobile device and so on. At the same time, very often an authentication message appears on the screen. Sometimes we do not even think about its importance and just do not pay attention to it. It would be nice to learn more about authentication. After all, this process protects our personal information from fraudsters.
Concept and types

Let us first consider the very concept of what isAuthentication. It is a verification or, in another way, verification of the authenticity of the user who is accessing a particular system. There are several types of this process:
One-sided and two-sided authentication.
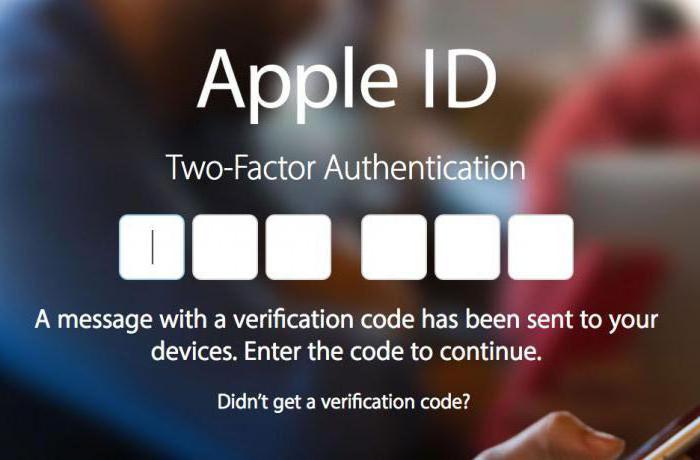
One-factor and multi-factor authentication. They differ in the number of methods used.
Static - while protecting user information when working with the site.
Stable - it provides protection against interception of the user's identity by applying dynamic ones.
Permanent authentication - verification requests occur at each stage.
Authentication methods
In more detail, the question of what authentication is, will help to consider the methods used in this process. There are several verification methods:
Using a password.
Combined - in addition to the password, other control attributes are used. It can be cryptographic documents, smart cards, e-tokens, mobile phones.
Using a scan or analysis of physiological characteristics. These are the so-called biometric methods of verification.
With the use of satellite communication - here the authentication process is carried out based on the confirmation of the location of the user using the GPS navigation system.

Principle of the process
The process of authenticating an object occurswhen attempting to log on to the system by the user, while requesting an identifier and secret information. An example using a one-time password most clearly reflects what authentication is. At each session, the user enters the login and password generated by the system. In addition, there are various ways to create this password. For example, characters change, but the input algorithm remains constant.
Systems providing security

At the moment there are different systemsauthentication, providing protection for various areas. At the same time, different system-programs use different methods, thereby achieving the most successful protection against information leakage. Thus, the Indeed-Id system is designed specifically to protect organizations from unauthorized access by outsiders. The system is based on strict authentication using various verification methods - and employees receive universal access.
Cases of hacking
However, with the development of control technologiesThe authenticity of the attack from the attackers became tougher. So, according to one of the employees of the German police Mirko Manske, cases of hacking accounts in banks have become more frequent. Moreover, authentication using two methods of verification does not justify itself, and funds continue to flow from the banks of Germany into the "pockets" of cybercriminals. Mirko Manske addressed the congress in London with a report on the insolvency of the system using iTan codes, which is used by almost all banking structures in Germany.
As can be seen, in conditions of intensified attacksIntruders require authentication with advanced data protection methods. Developers devise robust methods, but they are also able to find an approach and hackers.
</ p>